Archetype SC is a technology solutions company focused on finding the right solution for you biggest business challenges. We specialize in:
Technology Consulting Solutions
We do complicated.

"Archetype SC provided great insight and expertise on rebuilding our site, ensuring it looked great and functioned precisely to our specifications. They continue to offer expertise in design, development, user experience, and SEO. I confidently recommend their work."
Thomas CurtinPresident & Partner, Honeymoons.com
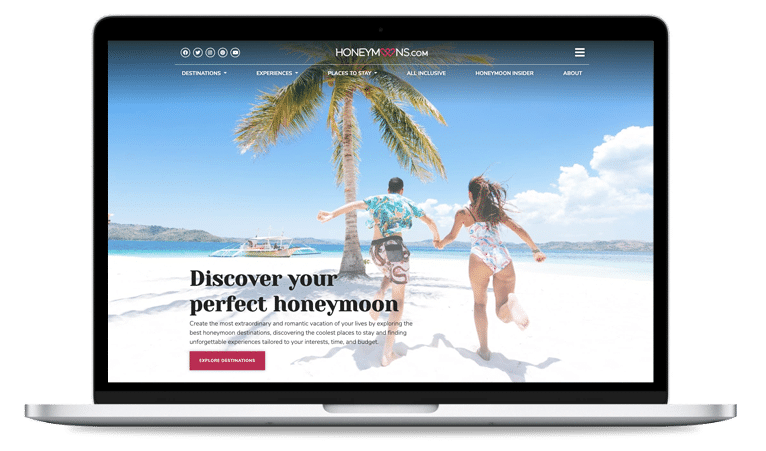 Refreshed Homepage design
Refreshed Homepage design "The expertise of their team is broad and each person we have interacted with has ensured our needs are met, every step of the way. Hands down, Archetype SC is my first call with any technology-related need."Mitch CorneliusTechnology Manager, Fortis Construction
"The expertise of their team is broad and each person we have interacted with has ensured our needs are met, every step of the way. Hands down, Archetype SC is my first call with any technology-related need."Mitch CorneliusTechnology Manager, Fortis Construction
- "The new system Archetype SC created has allowed us to achieve nearly 50% growth. Without their work, I’m confident we would not have been able to manage this growth and provide the same high level of service."Ray Trant
Executive Vice President, Odysseys Unlimited
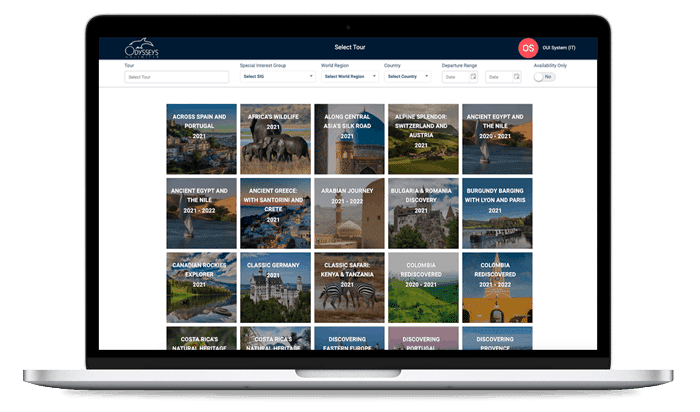

"I was impressed with Archetype SC every step of the way. They listened to our challenge, asked probing questions, inquired about budgets, and ultimately presented a custom solution ahead of schedule and within budget. "
Kirk LovellMyrtle Beach International Airport


"The Boston IT team exceeded the client's expectations, and receiving such appreciation from a client makes it even more special. It was an outstanding effort to deliver within the schedule and under budget, in spite of delays and other unforeseen constraints."
Shiva Kumar Kotthur
Competency Manager, Infrastructure and Endpoint Security


"Archetype SC modernized our internal systems, increased network security, and helped us take advantage of new technology for maintaining our website. The investment has been paramount to our customer experience."
Shannon FarroExecutive Director, Long Bay Symphony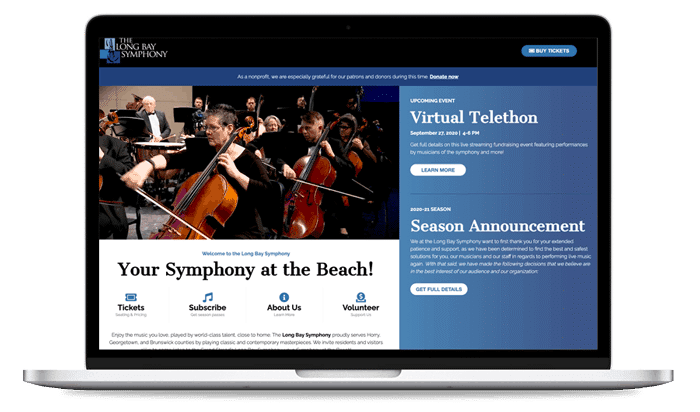
 "We have a partnership built upon years of trust, which gives us confidence in working together on any project. Their team is both consultative and technical, which is a unique combination. Providing customer satisfaction is the ultimate goal and Archetype SC delivers."Kyle Watson
"We have a partnership built upon years of trust, which gives us confidence in working together on any project. Their team is both consultative and technical, which is a unique combination. Providing customer satisfaction is the ultimate goal and Archetype SC delivers."Kyle WatsonManaging Partner, Cedrus Digital

WHAT WE DO
Technology solutions for every situation.
Cybersecurity
Whether you’re an enterprise with a security skills shortage, a small business needing to secure your data, or somewhere in between, the cybersecurity team at Archetype SC has the expertise and experience to solve your business challenges including:
- Networking & Firewall Management
- Identity & Access Management
- Threat Management
- Security Risk & Vulnerability Assessment


Digital Experience
Archetype SC provides full-stack Web, Desktop, and Mobile development services with a focus on user experience. Our team has deep expertise in building, delivering, and maintaining enterprise-level applications and providing technology solutions such as:
- Web Application Development
- iOS / Android Development
- Data Visualization & Reporting
- Data & Cloud Migration
- Digital Systems Integration

Websites & Design
At Archetype SC, design is in our DNA. Led by our co-founder, a UX designer with more than 20 years of experience on projects of all sizes, our team crafts user experiences that are functional, beautiful, and designed to meet your business goals. We specialize in:
- UX / UI Design
- Website Design
- WordPress Theme Development
- Branding & Logo Design

Data & Analytics
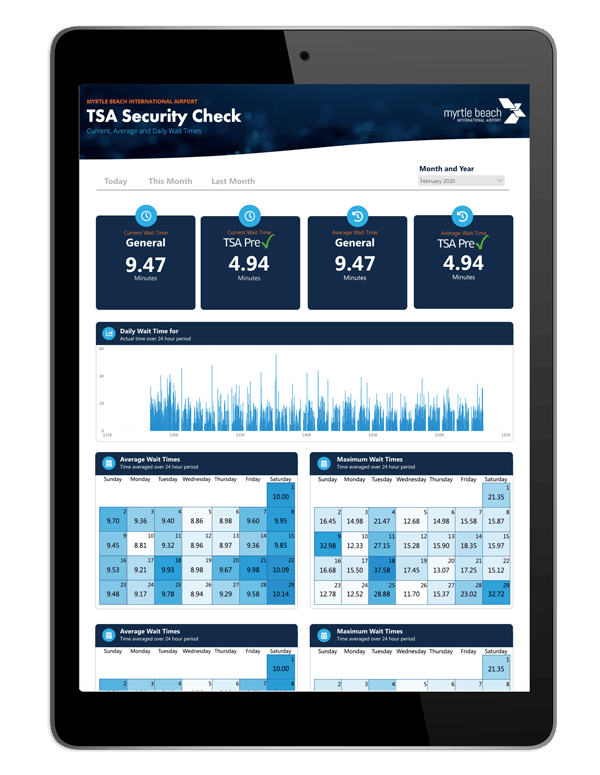
From dashboards to embedded reports and beyond, boost your business intelligence and guide data-driven decision making with custom data visualizations & reporting from Archetype SC. We can boost your business with solutions including:
- A2 Analytics
- PowerBI / Power Apps
- Custom Dashboard Development
- Data Strategy & Consulting

Digital Marketing
Archetype SC will help your business grow its reach, connect with its audience and convert leads into loyal customers. Our digital marketing services are backed by sound strategic guidance built on meeting your business goals and delivering insights on the KPIs that matter to you.
- Search Engine Optimization
- Social Media
- Content Marketing
- Conversion Rate Optimization


Technology Consulting
From tackling the most complex technical projects to providing expert analysis and business intelligence, Archetype SC's technology consulting team will provide the insight needed to drive your organization to new heights. We offer:
- Solutions Workshops
- Brand Strategy & Development
- Business Process & Root Cause Analysis
- Technology Selection
CLIENTS
Trusted by industry leaders.
Archetype SC applications are built to solve core business challenges and function flawlessly with user-centric design driven by sound research, data, and analytics. These are some of the many companies that have experienced growth by partnering with ASC on projects ranging from user experience to mobile development, progressive web application development, data analytics, cybersecurity, and business consulting.
- Medical
- Hospitality
- Information Technology

WHO WE ARE
No matter your type, we’re your archetype.
What's your archetype?
There are 12 master archetypes that define how people and businesses operate. Find out which archetype fits your business and how to leverage it to create digital connections with your customers.

 Joseph Bonanno,
Joseph Bonanno,
President & Co-Founder Usman Khan,
Usman Khan,
VP & Co-Founder Patrick Nord,
Patrick Nord,
VP of Professional Services
 Joseph Bonanno,
Joseph Bonanno,
President & Co-Founder Usman Khan,
Usman Khan,
VP & Co-Founder Patrick Nord,
Patrick Nord,
VP of Professional Services April Bogert Bonanno,
April Bogert Bonanno,
Director of Operations

What's your archetype?
There are 12 master archetypes that define how people and businesses operate. Find out which archetype fits your business and how to leverage it to create digital connections with your customers.
INSIGHTS
Digital transformation starts here.
Archetype SC is a trusted resource for strategic technology planning. We help you navigate a sea of trends and buzzwords so you don’t end up spending money on solutions that aren’t right for your needs. Our experts are dedicated to providing industry insights that will help you stay ahead of the technology curve.
CONTACT US
Let’s talk business.
Let’s be honest. If you’ve made it this far down the page you’re probably really interested in what Archetype SC has to offer (or you just really like to scroll). Why not set up a meeting and give us a chance to see how we can help you? It’s quick, easy and it could change the way your business uses technology forever.
OUR MISSION
We provide IT solutions and services to empower our clients to focus on growing their core business and their employees.
Contact Us
E-mail: info@archetypesc.com
Phone: (843) 353-2929
Address: 1012 38th Avenue N, Suite 301, Myrtle Beach, SC 29577

