On Monday, Dec. 3, Quora, a question-and-answer website where users can post and respond to inquiries with other users, announced it fell victim to a data breach where the personal data of up to 100 million users was accessed.
The breach follows a string of hacks over the weekend, with Marriott’s Starwood properties being the largest affecting as many as 500 million users.
Quora CEO Adam D’Angelo spelled out the company’s breach and response in a blog post, where he said the company was “very sorry for any concern or inconvenience this may cause.”
Some of the information accessed in the Quora breach includes account information such as names, email addresses, passwords, and data from linked networks like Facebook and Twitter. Additionally, public content and actions, like questions and answers, comments, and upvotes; and non-public content and actions like answer requests and direct messages, were included in the breach.
The company is working to investigate the root cause of the breach to avoid future issues with cyber security.
“It is our responsibility to make sure things like this don’t happen, and we failed to meet that responsibility. We recognize that in order to maintain user trust, we need to work very hard to make sure this does not happen again,” said D’Angelo in his blog post.
For your business, Archetype SC’s SRVA help to shore up security concerns by providing a comprehensive report of your network security, allowing your teams to easily understand potential threats. Our team of security experts works directly with your IT and management to remediate issues ensuring your security posture.
Contact us for a SRVA today.
Users of the Dunkin’ Donuts DD Perks account may have fallen victim to a data breach that was uncovered on Oct. 31 and announced publically Nov. 29.
The breach included customer names, email addresses, and DD Perks account numbers or codes for up to 9 million members. DD Perks members whose information fell victim to the breach were those who use the same passwords for multiple accounts, as the type of attack was a password reuse attack, where the cyber criminals attempted to use previously stolen login credentials to tap into DD Perks accounts.
While the attack on the DD Perks program was not a product of an internal system error by Dunkin’ Donuts, it shows how data breaches that hit other companies can then be utilized to attack businesses independent from the original attack. Additionally, this type of hack shows the importance of two-factor authentication and using unique login credentials for all accounts, both professionally and personally.
Preventing a cyber attack takes more than just good luck for your business. A great first step in ensuring your business is safe from cyber criminals is with Archetype SC’s Security Risk & Vulnerability Assessment, or SRVA. SRVA is a combination of a vulnerability scan and security assessment to show key issues facing your network, which are delivered in a comprehensive report broken down by severity. A member of Archetype SC’s expert security team will also present a remediation plan to improve your businesses security posture.
A weekend full of data breach announcements showed the wide-ranging impact of cyber criminals across industries, as major brands like Marriott, Dunkin Donuts, and the United States Postal Service announced attacks that impacted hundreds of millions of customers in total.
The largest of the breaches, Marriott’s Starwood properties, affected more than 500 million guests, with information including names, mailing addresses, phone numbers, email addresses, arrival and departure information, and communication preferences accessed by the cyber criminals. Also stolen in the breach were credit card numbers for more than 325 million customers, of which Marriott is unsure on the decryption status.
The Marriott breach began as far back as 2014.
For those who haven’t stayed at a Starwood by Marriott property, Dunkin’ Donuts and the USPS announced breaches that impacted up to 9 million and 60 million, respectively. At Dunkin’, data from the DD Perks program, including members’ names, email addresses, and account information, fell to a password-reuse attack. This form of attack includes cyber criminals using login and password information from other notable breaches to try and break into more accounts, highlighting the importance of two-factor authentication and unique, frequently updated passwords for accounts.
The USPS breach came about from a small security hole in a program that allows customers to preview their mail, looking for delivery and tracking information for critical documents and checks. Access to this program gives that crucial information to cyber criminals who are then able to steal identities, email addresses, phone numbers, and more from the data kept by USPS. This attack was said to be in the works for more than a year, with USPS only responding to the threat with a patch after a security expert asked about the breach that was alerted by an anonymous researcher.
If a major hotelier, restaurant, and government agency, which each spend millions of dollars a year on cyber security, can fall victim to a large breach taking place over months or years, small businesses are an easy victim for hacks and breaches.
Archetype SC has developed a vulnerability assessment, call SRVA (Security Risk & Vulnerability Assessment) which scans the network of a company to find potential security holes, like the ones that led to the large data breaches at Marriott, Dunkin’ Donuts, and USPS. After a SRVA is performed, a detailed report of vulnerabilities, ranked by severity, is delivered with a remediation plan. The assessment is done at low-or-no cost, with remediation as an optional piece.
Schedule a SRVA with Archetype SC today by emailing here.
As National Cybersecurity Awareness Month ends on Halloween, it presents the perfect time to remember some safety tips to keep the monsters, zombies, and mummies away from your network.
According to the 2017 Ponemon Cost of Data Breach Study, sponsored by IBM, the global average cost of a breach is $3.62 million, with more than 24,000 records affected per breach. For many businesses, a breach hits the bottom line in more ways than one, with a breach costing a third of companies about 20% of their customers, opportunities, or revenue (ITProPortal, 2016).
These 5 tips can help keep your network safe from things that go bump in the night, or lurk in the dark web:
Don't Click Links From Strangers
- While we're taught to never take candy from strangers (aside from Halloween night), opening links from unknown sources can be just as dangerous.
- Phishing scams are designed to make you think you're interacting with a trusted website, and will then attempt to collect login credentials, financial data, or account information.
- Rather than clicking a link in a suspicious email or message, try to verify the information with a trusted source, like a company website.
Protect Your Candy With a Strong Password
- As protecting your candy from the hands of the neighborhood bully, an older sibling, or your parents is crucial on Halloween night, so is creating and maintaining a strong, secure password.
- One of the best, and easiest, ways to ensure your accounts are kept secure is to create a strong password with upper and lowercase letters, numbers, symbols, and punctuation.
- It is also imperative to use different passwords for each of your accounts and to change them frequently, about every 6 to 8 weeks.
Chase Away Lurking Monsters
- While in the real world, most of the monsters are gone once Halloween is over, online monsters can infiltrate your computer for months unnoticed.
- Using a public Wi-Fi network at a restaurant, coffee shop, or town center can leave your computer vulnerable to attacks on your data.
- While using a public network, it is important to use a virtual private network (VPN) to encrypt traffic between your devices on public, unsecured networks.
Find a Costume for Your Personal Information
- Trick-or-treating without a costume is frowned upon, just like sending personal information online without encryption.
- Using a secured network or website keeps your information safe by converting it to an indecipherable code.
- Using a secure website (https) on your mobile device, rather than an app, allows for increased security.
Don't Leave a Candy Trail
- While you're out trick-or-treating, it is easy to quickly post a photo of a costume, your candy stash, or creepy decorations you may have seen.
- For many social networks, like Instagram, Twitter, Facebook, Snapchat, and more, location services are part of the package with using the app.
- With more GPS-enabled devices being used each day, your location information can give cyber criminals data on when you're away and where you're going, giving them a window to hack your personal information.
For more information on securing your network, contact Archetype SC to speak with an expert security engineer.
An unprecedented cyber-attack took the world by storm over the weekend, affecting more than 200,000 systems in 150 countries by targeting unsupported and unpatched versions of Microsoft Windows operating systems.
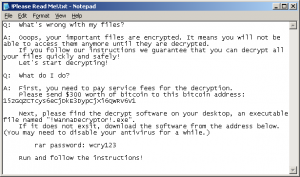
The attack, known as WannaCry, came in the form of a ransomware virus, which takes control of a computer and locks files. To unlock your files, the creators of WannaCry required a ransom of $300 be paid (in bitcoin) for the first three days of the attack. If the $300 was not paid in the first three days, the ransom amount doubled to $600. According to the warning, if the ransom were not paid within a week, the hackers said they would delete the files that were held ransom.
According to Symantec, the WannaCry virus targets more than 175 file types, including website and server files, documents, photos, videos, music files, and many other common and less common file types.
The virus spreads within a network by scanning for other vulnerable computers once it gains access to a first computer. It also scans hosts on the Internet to spread as quickly as possible.
Microsoft introduced a patch for the vulnerabilities WannaCry exploits, but this can only be installed in advance of the virus.
WannaCry primarily targeted Russia, Ukraine and Taiwan, but also affected hospitals in the United Kingdom, universities in China, and worldwide businesses like FedEx and Nissan.
The WannaCry virus is just the latest example in how a cyberattack can take over a computer network and stop business. If you’re concerned about your company’s vulnerability, the team at Archetype SC can help. Our team provides managed services and security solutions for some of the largest companies in the world and have the knowledge and experience to assist your company.
The first step to securing your network and computers is a security assessment. Call Archetype SC at (843) 353-2929 to review your concerns or schedule your assessment today.
Welcome to the latest installment of “Securing Your Windows Infrastructure”. Today’s topic is encryption – specifically encryption as it pertains to Active Directory. As with other applications, data managed by AD can be encrypted in storage and in transit. Let’s take a quick look at where encryption is, and can be, used by AD.
Replication Traffic
Luckily, replication traffic is encrypted by default, so there is nothing additional to do to keep data managed by AD secure as it goes over the wire. Kerberos v5 is used in this process, both for authentication of replication peers and encryption of replicated traffic.
LDAP Traffic
LDAP and Global Catalog (GC) traffic can also be encrypted. LDAPS is enabled simply by adding a Server Authentication certificate to the server’s Personal Certificate store. There are a number of requirements for the certificate that are outlined in the following Microsoft Support article: https://support.microsoft.com/en-us/kb/321051.
Active Directory Data Store
With the enhanced virtualization support for Active Directory in Windows Server 2012, you may now be running your DCs safely in a virtual machine. Keep in mind that although you can encrypt the drive of a Domain Controller using Bitlocker on a physical machine, it is NOT recommended to encrypt the drive of a VM from within the guest OS. Instead, the host can be configured to encrypt the drive containing the .vhd(x) files. This way, even if the drive is stolen, your data within the .vhd file will be safe.
Using EFS to encrypt ntds.dit may seem like a good idea at first, but because AD is needed to decrypt the file in the first place, a dangerous situation can result if this method is used.
Conclusion
It is easy to further enhance the security of Active Directory and your Windows Infrastructure by enabling a couple of the built-in tools that Microsoft includes with Windows. For assistance with encryption, Windows Security, or any other concerns, please get in touch with us using the Contact page of this website.
Every day, week, or month that passes we in the security community watch company after company get breeched by hackers or make the news with some other large scale security incident. If you work in the enterprise environment, more than likely you work for a company that either has had a large scale security incident or will have one in the future. Some corporations are taking proactive steps to make sure that they are not the next ones to make the news and the number of these corporations is on the rise as study after study shows the direct and in-direct costs that come with a data breach.
IBM recently published a study highlighting the cost of a corporate data breach in 2015 and the results speak for themselves. The study was the product of 1500 interviews spanning 11 countries, 350 companies in 27 industries, and concluded that the average cost of a breach is $3.8 million per breach, per company worldwide. In the healthcare industry in the U.S. that number more than doubles with the average cost of a breach at $6.5 million.
Global Study at a Glance:
• 350 companies in 11 countries
• $3.79 million is the average total cost of data breach
• 23% increase in total cost of data breach since 2013
• $154 is the average cost per lost or stolen record
• 12% percent increase in per capita cost since 2013
US Study at a Glance:
• 62 companies participated
• $6.5 million is the average total cost of data breach
• 11% increase in total cost of data breach
• $217 is the average cost per lost or stolen record
• 8% increase in cost per lost or stolen record
Study link: http://www-03.ibm.com/security/data-breach/index.html
Infographic link: http://www-03.ibm.com/security/infographics/data-breach/
Studies like these are showing C-suite executives the value in adopting new technologies to combat the advanced persistent threats that cost enterprises billions every year. When an enterprise has made the decision to invest in security, one of the areas often overlooked is who will analyze the information these tools capture once put into place. Time and again we have seen retrospective studies that show breaches could have been stopped if the tools they had in place had been properly managed. At Archetype SC we emphasize having policies and procedures in place to prevent, stop, and react to a potential breach or incident. We have experts in all facets of enterprise security and work with organizations to manage their security posture so they do not end up as tomorrow’s headline.
For some time, major companies have been moving away from a single password as a method of authentication and moving towards multifactor authentication or secure methods such as biometrics or behavioral techniques. The issue companies are attempting to address is password strength and integrity. Enforcing password etiquette and policy across numerous users is not easy, which leads some to conclude a single password is obsolete, and poses a much greater risk compared to a biometric scan or RSA token. While many still agree that the password is still an important layer of authentication the argument is quickly becoming that passwords are simply too basic to serve as true security measure.
The process of authorization is taking something you know, are, or have and using that data to prove your identity. Passwords have a much greater risk of being compromised compared to a fingerprint or an iris scan. No method works 100% of the time so the password layer, if implemented properly, still may be used in tandem with other, more secure methods of authentication. Though passwords may continue to plague us forever, innovations in authentication methods like biometrics and adaptive behavioral techniques will continue to shape the way we access our data in the future.
Fishing guides are a secretive bunch. Their livelihood depends on finding good fishing spots then taking paying clients to them. If we fish, we know good fishing spots are at a premium. Every fishing guide knows he or she is having a bad day when they and their client, show up at a fishing spot to find someone there before them. I've been on both sides. If you haven't experienced it, trust me. It isn't a good situation.
So, what does this have to do with cyber security? Many fishing guides have websites where you can learn about the their fishing service and book your trip. Fishing guides are also heavy users of Facebook to post pictures of a client's most recent catch.
Guides have quickly learned to take a picture of a client's catch, at an angle so there are no background features that might help identify the location. They understand, every posted picture will be scrutinized for details that give away where that fish was caught.
What can we learn from fishing guides?
Whether we're an individual or organization, most of us have a presence on social media. If we post anything on social media, our text and visual posts contain detail we might not want the internet audience to view. It's advice we've heard hundreds of times but it bears reinforcing. Review each post before you broadcast it. Every day, I view posts with personal detail that shouldn't be broadcast. You do too.
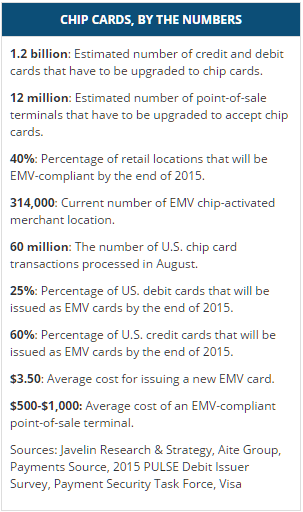
You likely have heard about the new shift in the credit card industry from magnetic strip to EMV chip cards. These cards have a small chip in them that facilitates communication to the payment card company in place of the magnetic strip technology that has been the industry standard for 25+ years. Historically, the motivating factor in large data breaches has been static data associated with payment cards. Once a thief breaks whatever security measure are in place and clones the magnetic strip of unsuspecting card holders that clone can be used over and over again which turn the fruits of the hacker’s labor into cash.
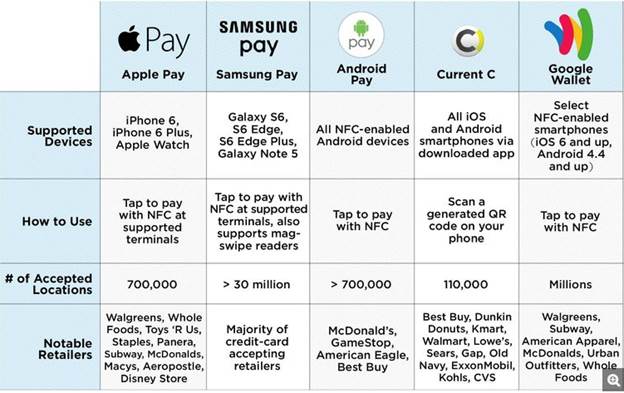
That is about to change once the swipe is replaced with the dip. The major security benefit of EMV is that every time you make a purchase, a new unique transaction ID is used to facilitate the transaction with the retailer. That transaction ID is unique to that sale and will never be used again, making the data retained by the retailer useless to a hacker. This payment model is the same deployed by mobile payment services like Android Pay, Apple Pay, and Samsung Pay. The difference between these three lies in how the information is transferred to the Point of Sale machine but the payment model of unique payment ID numbers is shared among them.
There will continue to be security risks, and EMV is not a cure-all pill. It does nothing to improve the security of online payments and not all retailers will have EMV POS machines at launch, leaving those retailers not only vulnerable, but heavy targets for hackers. Expect breaches aimed at smaller retail operations that do not have the means to upgrade their equipment at launch because EMV enabled cards can still be swiped if a POS machine is not able to process EMV payments. Europe has been using EMV for several years and credit card fraud has dropped by as much 80%, so it is clearly a step in the right direction.
Deloitte and RSA presented a collection of seven articles on risk, covering topics ranging from general business risk to IT specific risks.
As I read the articles, the definition of risk that I learned way back in a risk management class kept coming to mind. Definition: a risk is a potential future event that has a probability and an impact. The probability describes the likelihood that the future event will occur. The impact is either the positive or negative result if the event occurs.
The reason that the definition kept coming to mind is that many of articles seemed to miss some aspect of weighing the probability and impact of a risk as the first step in determining how to respond to the risk.
Several of the articles talk about the need to mitigate risk, and how to accomplish it, as though needing to mitigate the risk is a foregone conclusion. The only forgone conclusion of what should be done when a risk is identified, is to formulate a risk response strategy. One risk response strategy, when the impact of the risk is negative, is to mitigate the risk by lessening the likelihood of the event occurring, or limiting the negative impact that occurs. If the risk results in a positive impact, the strategy can be to increase the likelihood that the risk will occur.
Another risk response strategy is to simply accept the risk and not attempt to mitigate it. The cost of mitigating the risk may be excessive based on the likelihood that the risk event will occur and what the negative impact of the risk is.
For example, I’m aware of a major farm equipment manufacturer that did not have a backup IT disaster recovery site in the late 90s. Their risk analysis at that point in time told them it was too expensive to maintain a backup disaster recovery site based on the likelihood that their primary data center would be completely unavailable for an extended period of time. And if something occurred that took their data center offline for an extended period of time, it was likely that their manufacturing plants would also be impacted in a similar way, removing the immediate need for an operational data center to support them. This company’s Data Center Availability Risk Response Strategy was to accept the risk, not to mitigate it. The point is that risks need to be carefully evaluated and an appropriate risk response strategy formulated. There is not a one size fits all answer to risks and how to deal with them.
How do you handle risk analysis and formulating your risk response strategies?
In my experience as a security engineer, I have noticed that employees are often given significantly more access than needed. This is particularly true at large, enterprise level organizations. At enterprise clients I have worked with, I was responsible for granting this access once a request was approved. All too often I receive requests that clearly have not been investigated, with few, if any, questions asked as to why a user needs the access. Managers may believe themselves too busy or lack the technical expertise to investigate requests and approve them pro forma.
Asking a few simple questions, I have discovered that often users will submit a request for access simply because a colleague in a similar role has it, not based on an actual need. This is a problem—access should only be granted based on need. Even when a user does not have malicious intent, he or she may inadvertently cause chaos within a company’s IT infrastructure in areas they should not be able to access.
The solution is simple on paper, but can be difficult to implement. Managers or those granting access need to take the time to review requests, evaluate them to ensure there is a valid business need, and grant only the requests that meet a defined criteria. The world of cyber-threats is constantly changing, but carefully designed access management policies can help protect your valuable resources.