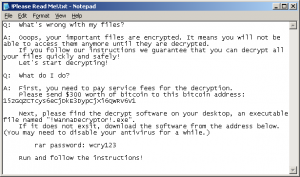
An unprecedented cyber-attack took the world by storm over the weekend, affecting more than 200,000 systems in 150 countries by targeting unsupported and unpatched versions of Microsoft Windows operating systems.
The attack, known as WannaCry, came in the form of a ransomware virus, which takes control of a computer and locks files. To unlock your files, the creators of WannaCry required a ransom of $300 be paid (in bitcoin) for the first three days of the attack. If the $300 was not paid in the first three days, the ransom amount doubled to $600. According to the warning, if the ransom were not paid within a week, the hackers said they would delete the files that were held ransom.
According to Symantec, the WannaCry virus targets more than 175 file types, including website and server files, documents, photos, videos, music files, and many other common and less common file types.
The virus spreads within a network by scanning for other vulnerable computers once it gains access to a first computer. It also scans hosts on the Internet to spread as quickly as possible.
Microsoft introduced a patch for the vulnerabilities WannaCry exploits, but this can only be installed in advance of the virus.
WannaCry primarily targeted Russia, Ukraine and Taiwan, but also affected hospitals in the United Kingdom, universities in China, and worldwide businesses like FedEx and Nissan.
The WannaCry virus is just the latest example in how a cyberattack can take over a computer network and stop business. If you’re concerned about your company’s vulnerability, the team at Archetype SC can help. Our team provides managed services and security solutions for some of the largest companies in the world and have the knowledge and experience to assist your company.
The first step to securing your network and computers is a security assessment. Call Archetype SC at (843) 353-2929 to review your concerns or schedule your assessment today.
Welcome to the latest installment of “Securing Your Windows Infrastructure”. Today’s topic is encryption – specifically encryption as it pertains to Active Directory. As with other applications, data managed by AD can be encrypted in storage and in transit. Let’s take a quick look at where encryption is, and can be, used by AD.
Replication Traffic
Luckily, replication traffic is encrypted by default, so there is nothing additional to do to keep data managed by AD secure as it goes over the wire. Kerberos v5 is used in this process, both for authentication of replication peers and encryption of replicated traffic.
LDAP Traffic
LDAP and Global Catalog (GC) traffic can also be encrypted. LDAPS is enabled simply by adding a Server Authentication certificate to the server’s Personal Certificate store. There are a number of requirements for the certificate that are outlined in the following Microsoft Support article: https://support.microsoft.com/en-us/kb/321051.
Active Directory Data Store
With the enhanced virtualization support for Active Directory in Windows Server 2012, you may now be running your DCs safely in a virtual machine. Keep in mind that although you can encrypt the drive of a Domain Controller using Bitlocker on a physical machine, it is NOT recommended to encrypt the drive of a VM from within the guest OS. Instead, the host can be configured to encrypt the drive containing the .vhd(x) files. This way, even if the drive is stolen, your data within the .vhd file will be safe.
Using EFS to encrypt ntds.dit may seem like a good idea at first, but because AD is needed to decrypt the file in the first place, a dangerous situation can result if this method is used.
Conclusion
It is easy to further enhance the security of Active Directory and your Windows Infrastructure by enabling a couple of the built-in tools that Microsoft includes with Windows. For assistance with encryption, Windows Security, or any other concerns, please get in touch with us using the Contact page of this website.
Fishing guides are a secretive bunch. Their livelihood depends on finding good fishing spots then taking paying clients to them. If we fish, we know good fishing spots are at a premium. Every fishing guide knows he or she is having a bad day when they and their client, show up at a fishing spot to find someone there before them. I've been on both sides. If you haven't experienced it, trust me. It isn't a good situation.
So, what does this have to do with cyber security? Many fishing guides have websites where you can learn about the their fishing service and book your trip. Fishing guides are also heavy users of Facebook to post pictures of a client's most recent catch.
Guides have quickly learned to take a picture of a client's catch, at an angle so there are no background features that might help identify the location. They understand, every posted picture will be scrutinized for details that give away where that fish was caught.
What can we learn from fishing guides?
Whether we're an individual or organization, most of us have a presence on social media. If we post anything on social media, our text and visual posts contain detail we might not want the internet audience to view. It's advice we've heard hundreds of times but it bears reinforcing. Review each post before you broadcast it. Every day, I view posts with personal detail that shouldn't be broadcast. You do too.
Deloitte and RSA presented a collection of seven articles on risk, covering topics ranging from general business risk to IT specific risks.
As I read the articles, the definition of risk that I learned way back in a risk management class kept coming to mind. Definition: a risk is a potential future event that has a probability and an impact. The probability describes the likelihood that the future event will occur. The impact is either the positive or negative result if the event occurs.
The reason that the definition kept coming to mind is that many of articles seemed to miss some aspect of weighing the probability and impact of a risk as the first step in determining how to respond to the risk.
Several of the articles talk about the need to mitigate risk, and how to accomplish it, as though needing to mitigate the risk is a foregone conclusion. The only forgone conclusion of what should be done when a risk is identified, is to formulate a risk response strategy. One risk response strategy, when the impact of the risk is negative, is to mitigate the risk by lessening the likelihood of the event occurring, or limiting the negative impact that occurs. If the risk results in a positive impact, the strategy can be to increase the likelihood that the risk will occur.
Another risk response strategy is to simply accept the risk and not attempt to mitigate it. The cost of mitigating the risk may be excessive based on the likelihood that the risk event will occur and what the negative impact of the risk is.
For example, I’m aware of a major farm equipment manufacturer that did not have a backup IT disaster recovery site in the late 90s. Their risk analysis at that point in time told them it was too expensive to maintain a backup disaster recovery site based on the likelihood that their primary data center would be completely unavailable for an extended period of time. And if something occurred that took their data center offline for an extended period of time, it was likely that their manufacturing plants would also be impacted in a similar way, removing the immediate need for an operational data center to support them. This company’s Data Center Availability Risk Response Strategy was to accept the risk, not to mitigate it. The point is that risks need to be carefully evaluated and an appropriate risk response strategy formulated. There is not a one size fits all answer to risks and how to deal with them.
How do you handle risk analysis and formulating your risk response strategies?
In my experience as a security engineer, I have noticed that employees are often given significantly more access than needed. This is particularly true at large, enterprise level organizations. At enterprise clients I have worked with, I was responsible for granting this access once a request was approved. All too often I receive requests that clearly have not been investigated, with few, if any, questions asked as to why a user needs the access. Managers may believe themselves too busy or lack the technical expertise to investigate requests and approve them pro forma.
Asking a few simple questions, I have discovered that often users will submit a request for access simply because a colleague in a similar role has it, not based on an actual need. This is a problem—access should only be granted based on need. Even when a user does not have malicious intent, he or she may inadvertently cause chaos within a company’s IT infrastructure in areas they should not be able to access.
The solution is simple on paper, but can be difficult to implement. Managers or those granting access need to take the time to review requests, evaluate them to ensure there is a valid business need, and grant only the requests that meet a defined criteria. The world of cyber-threats is constantly changing, but carefully designed access management policies can help protect your valuable resources.
Overview
“Game of Thrones” fans are very familiar with the Dyre Wolf. I am not, however; referring to the Dyre Wolf that is the blood thirsty animal from the Pleistocene Age. What it is though, is just as hungry and its prey is your money. Researchers at IBM recently released a white paper titled “Inside the Dyre Wolf Malware Campaign,” which describes a sophisticated attack against bank accounts of major corporations worldwide. This campaign was well funded, well planned and executed perfectly. The attackers had a high level of knowledge regarding banking systems and websites. The attack used a diverse combination of attack vectors including spear phishing, malware, complex process injections, and distributed denial of service (DDoS).
The Spear Phish
An email was sent to an employee within the targeted organization. The email referenced an invoice and included an attached zip file. Once the zip file was unpacked it contained what looked like a .pdf document. Most users choose not to have their computer show all file extensions and so a user was unable to see the actual extension of the file—.scr. Once clicked the script, which was actually a piece of malware called UPATRE (pronounced up-a-tree), ran and so began the infection.
First Stage Infection
UPATRE performs a DNS check to determine the public IP address of the infected machine. Then, it contacts a STUN (Session Traversal Utilities for NAT) server to determine the type of NAT in use. It determines if the infected computer is behind a proxy by contacting Google.com and makes contact with its command and control server to download the Dyre malware. Once Dyre is loaded, UPATRE then deletes itself.
Second Stage Infection
The Dyre malware creates a service called Google Update Service to establish persistence on the machine. This service runs when the machine is started. On restart Dyre injects malicious code into the SVCHOST.EXE process before stopping the Google Update Service. Next, Dyre makes connections to several different I2P nodes and establishes encrypted peer-to-peer tunnels to send its information undetected. Then, Dyre hooks the machines browsers in order to steal credentials. It is only looking for credentials for specifically targeted banking sites. If Microsoft Outlook is detected on the machine, Dyre attempts to replicate itself by sending the infecting message to addresses in the contact list.
Dyre uses three different methods to steal credentials. In the first method, if the user browses to one of the targeted banking sites it uses server side injections to create additional fillable fields in order to capture personally identifiable information and two-factor authentication codes. The second method involves routing the infected user’s traffic through a proxy to Dyre’s command and control server where a replica of the banking page is delivered to the user. This fake site also contains the additional form fields used to capture banking credentials. The third method is the most sophisticated. Dyre intercepts responses from the banking website and using its own PHP server it serves code injected responses to the user in real time. This means that the victim is communicating directly with the attackers, live.
For high value targets Dyre has one additional attack method. When the victim attempts to browse to the targeted banking site Dyre injects the page with an error message. The error contains a customer service number to contact. This number is controlled by the attackers. When the user calls to fix their access they are greeted by a well-trained and well-spoken individual who asks the user to provide their credentials and two-factor codes in order to fix their access to the site. Once the attacker has all the information they need to access the account they then tell the user to wait 10 minutes for the system to update before attempting to log back into the account. It is during this time the attackers log into the account and transfer large sums of money, values between $500,000 to over $1,000,000 have been reported.
The DDoS
Once the attackers complete the transfer they issue a DDoS attack against the targeted organization. Researchers suspect that this serves to distract the organization, prevent the victim from logging into the banking site to discover the transfer, and to cause additional financial damage to the organization.
How can you prevent this?
First, organizations should strip executables from e-mail attachments. Additionally, executables should be stripped from archive files like .zip. Next, organizations should ensure that their antivirus products are updated regularly. Organizations should also prevent executables from running inside temp directories. This can be accomplished using Group Policy Objects in Active Directory. Infected machines should be rebooted after remediation to prevent Dyre from running in memory. Two-factor authentication should be used whenever possible, especially for internet banking websites. Lastly, user education is important. Users should regularly receive training regarding what is normal to see in the work environment, what actions should or shouldn’t be taken, and where and how to report anomalies.
Archetype SC’s security team is expert at helping companies navigate the complicated world of IT security and prevent attacks like the Dyre Wolf. If you have concerns, give us a call. Archetype SC, we do complicated.
Application whitelisting (AWL) is a technology that has been used in the security industry for a long time but is not yet widely accepted in enterprise workstation environments. AWL is the opposite of blacklisting which is the model used in most antivirus software today. Traditional antivirus looks for malicious files by fingerprinting files on the system and checking those fingerprints against a registry of known malware (the blacklist). Antivirus also looks at other variables and file behaviors to decide whether an intervention is needed. That intervention is the antivirus adding that file to the local blacklist. Application whitelisting is different.
Whitelisting operates on a no trust, “default deny” model which does not allow any code to run on the system unless it has been explicitly added to the list of executables known to be NOT malicious. With whitelisting software becoming more advanced and enterprises growing wearier of being attacked this technology is on the rise. If you are not whitelisting at least your critical enterprise servers, you should be. Most industry experts would agree that deploying whitelisting software like McAfee Application Control is the single best way to secure an endpoint from being attacked. The reason every server, workstation, and the mobile device does not use this technology is that it needs to be properly managed.
Deploying a whitelisting program in production is a daunting task that will be met with skepticism throughout the enterprise because people generally do not like to be told what they can and cannot run on their workstations. Getting management support and developing well thought out policies to deal with the inherent issues that will come up once you go live is vital.
Starting a pilot program on enterprise servers that generally do not change much is a great place to start. The way AWL works is you either take a snapshot of a system and all of its executables to create your whitelist or you can use the corporate gold image if one exists. The next step is to turn on the technology in audit mode to allow time for establishing a baseline.
This step allows changes to be made to the system but logs them for review. Generally, 2 – 4 weeks is a good amount of time to get a good picture of what the systems normal behavior looks like. The final step when you lock down the system is establishing policy to decide what happens when the end user tries to execute a program not on the whitelist. There should be a review team able to make decisions in a reasonable amount of time. Every successful AWL deployment will have a dedicated team to deal with approval requests and the management overhead. At ArchetypeSC we have experienced professionals that can give your enterprise the upper hand against the persistent threats attacking networks constantly. When a hacker gains access to a system they need to run tools to successfully achieve their objective. If the tools aren’t able to run because of a whitelisting policy, then the chances of your enterprise having a breach have been drastically reduced.
Not too long ago most people were unaware of how valuable their personal data was and the impact it could have on one’s life when it fell into the wrong hands. All too many people can say they have firsthand experience with the rise in the past 10-15 years of identity theft. Simply being aware of the existence and risk of identity theft can greatly reduce a person's risk of falling victim. Proactively making people aware of the risk they face, often unknowingly, can also reduce their exposure to identity theft.
This is interesting, but you may be wondering why I am writing about this on Archetype SC's IT security blog. When you look at the old model security teams, it involved waiting for something to break then fixing the issue.
A proactive mindset takes the approach to anticipate and solve problems before they arise. In today’s world, with the vast amount of security applications and one stop shop providers, it is incumbent on the provider to provide updates with fixes, both proactive and reactive. With that being said, security teams still play a crucial role in the sector by assessing where the next attack going to happen and how to mitigate them before they take place. By taking a proactive approach toward your security and systems you can fix things before they have the chance to break.
If you need help securing your infrastructure or would like a proactive security assessment, contact the team at Archetype SC. Archetype SC: we do complicated.
In this edition of our “Securing Your Windows Infrastructure” series, I’ll be talking about some great free tools offered by Netwrix. Netwrix was founded in 2006 and offers a comprehensive suite of commercial and free security tools, all focused around increasing visibility into the changes made to your Windows environment.
Among their free tools, you can find Netwrix Change Notifier for Active Directory, Netwrix Effective Permissions Reporting Tool, and Netwrix Change Notifier for File Servers. The two change notification applications should be considered essential in any organization where multiple people have administrative access to Active Directory and member servers, and the permissions reporting tool will increase visibility into the rights that have been granted to a user throughout your infrastructure.
Netwrix Change Notifier for Active Directory will give you “Complete Visibility into Who Did What, When and Where in Your Active Directory”. As with all of the freeware software offered by Netwrix, there are some limitations. Without a license you will not see who made a change, but you can still gain insight into the changes made in your environment, roughly when the change was made (based on when the report was generated), and which objects were affected.
Netwrix Effective Permissions Reporting Tool is a new freeware offering with no commercial counterpart. Using this application, you can scan your servers for the rights held by a specific user. After the scan is complete, you will be presented with a report that clearly shows the objects the user has permissions to, their level of access, and via which group(s) the access is gained. At this point, the tool is good for one-off scans or periodic audits, but I’m hoping to see a more feature-full commercial version in the near future.
Lastly, Netwrix Change Notifier for File Servers is very similar to Netwrix Change Notifier for Active Directory, but as you may have guessed, it targets file and folders, detailing changes to both permissions and additions and deletions to the file system. As with Netwrix Change Notifier for Activec Directory, you must upgrade to the commercial version to see who made the change and when.
If you weren’t familiar with Netwrix, I hope this quick introduction to a few of their most popular products was helpful and will give you a new level of insight into the changes made and permissions in your Windows environment. As always, feel free to contact Archetype SC at any time for assistance with auditing, Windows security, or any of the number of other services we offer.
The InfoSec community has seen a rise in attention grabbing names for security vulnerabilities over the last couple years like Heartbleed, Freak, Shellshock, and now the latest android vulnerability Stagefright. The Stagefright exploit is different though, its name is derived from the media engine baked into android OS since version 2.2. The Stagefright engine is built into the application framework of android making it a part of your android OS no matter what country you live in, wireless carrier you use, or what brand of phone you buy. It is estimated there are 950 million devices vulnerable to a Stagefright attack.
The most alarming issue about this exploit is that it can be executed with no end-user interaction. An attacker simply has to send an mms message with malicious code written into a video and the device automatically begins to process the code, setting the attack in motion. Further complicating matters is most manufacturers default settings which are set to auto-retrieve mms messages. The user may not even know they were attacked because after the exploit gains root access of the phone the message is deleted but the malicious code stays.
The Stagefright media engine runs with system privileges on roughly 50 percent of the affected devices making it easy to gain root access to the device. Gaining root access on an android phone is the holy grail of exploits and the damage that can be caused is only limited by the attacker’s imagination.
Android is an open source OS which some might say makes it more secure while others would argue the opposite. The security architecture built into system applications in android take the sandbox approach. Most system apps are designed to be contained within themselves so attacks like the Stagefright exploit are not possible. This brings up the question of why the Stagefright engine has access to the internet and can be executed without the user’s knowledge. The answer is the DRM (Digital Rights Management) copyright control technologies that have been implemented over the last decade have required media players to make sure the content is being played legally. The technologies used to protect the content often require media players to check in via the internet, leaving a door open for malware.
Google has already began patching its Nexus line of phones and tablets with Samsung following as well. The inherent problem with android OS is that it is segmented into thousands of different variations of devices and carriers which makes patching a security hole like this a difficult task. Carriers like AT&T and Verizon control the software updates that get pushed out to their customers further complicating the matter. If there is a silver lining in this exploit being brought forth it is that Google and Samsung are going to begin delivering monthly security updates to devices. This is a step in the right direction for mobile device security.
Here is how to protect yourself from falling victim the Stagefright exploit:
Android Kitkat – Open the messenger app and in the settings menu select “block unknown senders”
Android Lollipop – Open the messenger app and turn off Auto-Retrieve for multimedia messages.
The CyberSecurity Information Sharing Act of 2015 (CISA), is a law currently circulating through Congress in draft form. In a nutshell it is supposed to allow the sharing of threat indicators both to and from the federal government and private entities and corporations. The bill has been met with opposition, primarily from the ACLU (American Civil Liberties Union) and the EFF (Electronic Frontier Foundation).
The main concern is of course consumer privacy. The bill in its current form provides a blanket authorization for companies to monitor the internet activity of all of their users. That in itself doesn’t seem so bad since companies already have that authority. However, another provision in the bill requires the instantaneous sharing of that information with military and intelligence agencies like the NSA.
Is CISA starting to sound like a “cyber-surveillance” bill yet?
The bill does not require the sanitization of Personally Identifiable Information (PII) prior to transmission to government agencies. CISA also does not limit sharing only of cybersecurity information but also a wider range of offenses including crimes involving any level of physical force without that force causing bodily injury or death. One additional provision permits companies to take action against users (even innocent ones) without regard to the potential harm that could be caused.
The icing on the cake is that the bill also incorporates immunity to corporations from potential lawsuits further increasing the likelihood that the provisions in the bill will be acted on.
The Center for Democracy & Technology has written a letter to the Senate Select Committee on Intelligence outlining the objections of civil society organizations, security experts and academics and it can be viewed here: https://cdt.org/insight/letter-to-senate-select-cmte-on-cisa/
I am all for information sharing in the modern age that allows for the protection of consumer interests. However, how much of our rights to privacy should we throw away in order to “feel” safe?
Today we will be taking a look at some of the recent security issues Adobe has been including Adobe's recently-issued security advisory APSA15-02
Summary
A critical vulnerability (CVE-2015-0313) exists in Adobe Flash Player 16.0.0.296 and earlier versions for Windows and Macintosh. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system. We are aware of reports that this vulnerability is being actively exploited in the wild via drive-by-download attacks against systems running Internet Explorer and Firefox on Windows 8.1 and below.
Most people are aware of the security risks of running plugins like Java and Adobe Flash in their browser so it comes as no surprise when we see criminals using vulnerabilities in these plugins along with exploit kits such as Angler and malvertising schemes to further their illegal activity. Adobe announced a 0-day vulnerability in Adobe Flash Player version 16.0.0.296 delivered by an exploit kit called HanJuan. The vulnerability is caused by a bug in how Flash handles the FlashCC ”fast memory access” feature (domainMemory), when the last is used by flash Workers (flash threads). So this attack per TrendMicro was delivered through malicious advertisements served in popular websites like Dailymotion, Wowhead, Answers.com and redirected to multiple sites that ended up leading to the URL “hxxp://www.retilio.com/skillt.swf”.
Recently the Angler Flash zero day (CVE-2015-0311) was discovered by a French researcher named Kafeine . We have also seen other exploit kits besides for Angler like RIG and Nuclear Pack taking advantage of CVE-2015-0311.
Cisco has reported that 1,800 domains have been compromised using Angler and have been associated with exploits and the landing page. We have also seen Flash zero day exploit code in Angler that was installing click-fraud malware called Bedep and using that as a dropper to be used to install malicious files. We are also seeing that this exploit code was hidden among several layers of obfuscation to avoid detection.
So exploit kits are dangerous since they have the ability to turn web servers into a launching pad for drive-by installs. In most instances simply visiting one of these web pages that have been poisoned can result in remote control of your computer through an unpatched plugin or browser. Flash is an attractive target since it uses local storage to cache files and has the ability to send and receive data to remote targets which makes this exploit extremely dangerous. Flash cookies can be an appealing target since these can have credentials among other sensitive information in these data stores. You can view information from Shared Objects on the file system in the following locations. For Mac you can go to Library/Preferences/Macromedia/Flash Player/#SharedObjects folder that exists in your Home directory and on Windows the files exist in C:\Documents and Settings\[Username]\Application Data\Macromedia\Flash Player. My advice would be if you must use Flash and JVM plugins use whitelisting otherwise disable or uninstall them altogether. HTML5 flash is also another alternative in place of Adobe Flash.