Small businesses are the target of cyber attacks.
In terms of preparation, this may be news for some business owners.
In 2019, 58% of cyber attack victims were businesses with fewer than 250 employees or small businesses. Often, small businesses find themselves broiled in cyber attacks because of a “too small” mentality. Many business owners think they are too small to fall victim to a data breach and have budgets that are too small to combat the problem.
As data breaches and hacks have advanced, so has the need for proper security measures to protect business data.
QUESTION 1
Do your employees help or hurt your security?
- The problem: Human error accounts for 25% of data breaches and represents one of the largest weaknesses in security for most businesses.
- The solution: Regular training to recognize ransomware, phishing, and general security protocols are critical in the “all hands on deck” approach to security employed by small businesses.
QUESTION 2
How are your accounts secured?
- The problem: Poor passwords create one of the largest vulnerabilities for businesses, as more than 70% of passwords are recycled from other accounts.
- The solution: Implementing multi-factor authentication protects accounts by requiring more than just login credentials. Using a text message, tokens, or biometrics adds an additional layer of security to accounts.
QUESTION 3
Are you protecting your endpoints?
- The Problem: There were 10.5 billion malware attacks in 2018; antivirus software detects over 350,000 pieces of malware daily.
- The Solution: Antivirus software has been around for a long time but is still effective. While no antivirus software is 100% effective, having a platform in place can help detect and prevent malicious attacks.
QUESTION 4
Is your data backed up?
- The Problem: Ransomware attacks lock your data and demand money, with companies paying an average of $84,116 to recover data in Q4 2019.
- The Solution: Backing up your data from devices and the cloud locally and to an off-site server will protect your business from potential ransomware and system crashes.
QUESTION 5
Have you limited access to sensitive data?
- The Problem: More than 80% of organizations do not have a plan for privileged access management, leading to double to breaches.
- The Solution: Ensuring the data that runs your business is not open to all employees by using identity and access management technologies will mitigate risk when a data breach occurs.
Critical business data should not be accessible to all employees.
QUESTION 6
How is your network monitored?
- The Problem: 68% of data breaches take months, not days, to uncover for businesses, creating a larger impact and more expensive recovery.
- The Solution: Network monitoring tracks the entire IT infrastructure of an organization, providing an early warning system of potential threats.
QUESTION 7
What is your data recovery plan?
- The Problem: More than 60% of companies have experienced some form of data breach over the past two years, making it a when not if scenario for most businesses.
- The Solution: Creating an incident response plan organizes your employees to help recover from a breach and return to normal working conditions.
QUESTION 8
What are your vulnerabilities?
- The Problem: One in every three data breaches is the result of a vulnerability that should have been patched.
- The Solution: A vulnerability assessment can provide your organization with the knowledge of how a hacker would gain access to your network, giving you a head start to shoring up issues before they are exploited.
‘Tis the season for holiday gatherings, work parties, and family obligations, making it all too easy to forget about cybersecurity.
During the hustle and bustle of the holiday season, cybercriminals are on the prowl, looking to dupe the unsuspecting masses with scams to steal personal information, financial data, and other sensitive information.
How can your organization and its employees ensure your holidays are happy and your data remains protected?
Don’t use public Wi-Fi for sensitive information
Wi-Fi connections that are public can be accessed by anyone, thus leaving those networks open for fraudsters to pillage your data. In the era of online shopping via cell phones and tablets, more personal information like names, addresses, bank accounts, and credit cards are shared without a thought of encryption or security. Don’t open your wallet to cybercriminals by using public Wi-Fi to transmit your most valuable data.
Only use verified websites
Website security is a critical component to keeping your data safe, regardless of what deal you’re hunting. Trusted websites should have “https” at the beginning of the website and a lock image near the address bar, showing that the page is secure and encrypts all information that it is transmitting. Without encryption, your data is an open book for hackers.
Change your passwords
This might seem like the simplest activity that doesn’t hold much weight, but your login credentials open the door for cybercriminals to infiltrate a network or open accounts in your name. Even if you haven’t been breached in the past, which is unlikely, using the same login credentials across accounts is a recipe for disaster. Work to have unique passwords for all of your accounts, using software like LastPass to help create and store information. Many hacks come from credential stuffing attacks, where a hacker will use information stolen from previous breaches to try and infiltrate other accounts.
Be suspicious of email links
Yes, everyone gets thousands of emails around the holidays with promises of big sales, epic savings, and an opportunity that is too good to pass up. How often do you check to see that the sender is actually a representative of the business? Oftentimes, phishing scammers can make an email look identical to a legit one from your favorite brand, then include dummy links that lead you away from the savings and sales. Be ultra-careful to avoid falling down a phishing hole this holiday season.
We hope your holidays are a wonderful time spent with friends and family, not trying to recover accounts, change passwords, and replace compromised cards. Take an extra step in your security and enjoy the most wonderful time of the year!
In late February, two cybersecurity researchers happened upon one of the largest non-password protected email databases on the web.
Bob Diachenko and Vinny Troia of the website SecurityDiscovery.com, found the online database of email addresses and personal information with more than 150GB of data, totaling over 800 million records with limited-to-no security. Their astounding find rooted back to the email validation service company Verifications.io.
In the database, Verifications.io had three folders titled "businessLeads," "Emailrecords," and "emailWithPhone," with each making up millions of records. "Emailrecords" had nearly 800 million alone, while the other two folders had more than 4 million and 6 million, respectively. In addition to email addresses, "Emailrecords" also contained zip codes, phone numbers, addresses, gender, and date of birth information.
Diachenko alerted Verifications.io of the breach via a ticket on the company's website, which prompted the removal of the database from the web and a response from the company stating no personally identifiable information had been included in the records.
Verifications.io is an email validation service for marketing companies, which works by keeping records of deliverable emails and vetting addresses against a company's email list. The service will send an email to an address to see if it will be delivered or bounce back, then keep a record of active addresses for companies to utilize with marketing email campaigns. These services keep marketing companies from being flagged as spam by sending multiple emails in a short timeframe.
Protecting your email address is as simple as routinely changing the account password with a strong credential, using a secure email service, and selecting obscure (or false) information about yourself for security questions.
If you have concerns around business email security, contact Archetype SC's security team to set up a consultation for SRVA, our security assessment tool that can scan your network for vulnerabilities that could be exploited by cybercriminals.
More than $800,000 was stolen in a hack of the banking account information at Cape Cod Community College in Massachusetts, showing yet again that data breaches happen to businesses of all sizes, not just large enterprises.
On Friday, Dec. 7, school president John Cox informed faculty and staff of the breach, saying that many computers in the Nickerson Administration Building were hit with a phishing attack that used malware to infiltrate the school's accounts. The malware was used to steal banking information and transfer money away from the institution.
According to the Boston Globe, the school has recovered about $300,000 of the funds, working with TD Bank and law enforcement officials. Other attacks on the school's network have been prevented by school officials, who have also replaced all infected hard drives from the breach.
The attack started with an Internet outage that the school believed was an issue with its provider.
To protect against future attacks, "Four C's" is working with local and national law enforcement to trace the roots of the attack, upgrading security measures campus-wide, and offering more training to employees on what to look for in a hack.
"This attack on our College’s security demonstrates the power and danger of modern cybercrime," Cox wrote to faculty and staff. "Despite ongoing cyber security training and continuous upgrades to the College’s network security, those with the power to execute a sophisticated malware attack found a way to do so."
Cox's email states that no personally identifiable information or records were impacted and all financial services are still fully operations.
Data breaches come in many forms, with some recent attacks using phishing, password reuse, and database hacking. Over the past month, large companies have been hit, affecting millions of users, but small businesses and even colleges are under constant threat of breach. If your business hasn't had a cyber security assessment or audit recently and uses the Internet, you are susceptible to an attack.
Consider a SRVA by Archetype SC, which includes an internal scan on-site, a qualitative assessment of security practices, and an external scan from our offices. A deliverable report highlighting critical vulnerabilities will be provided to you, with a remediation plan to remedy any gaps uncovered in your security efforts.
Email srva@archetypesc.com to schedule your assessment.
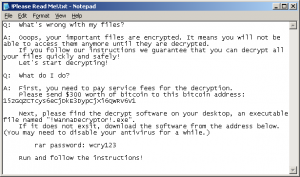
An unprecedented cyber-attack took the world by storm over the weekend, affecting more than 200,000 systems in 150 countries by targeting unsupported and unpatched versions of Microsoft Windows operating systems.
The attack, known as WannaCry, came in the form of a ransomware virus, which takes control of a computer and locks files. To unlock your files, the creators of WannaCry required a ransom of $300 be paid (in bitcoin) for the first three days of the attack. If the $300 was not paid in the first three days, the ransom amount doubled to $600. According to the warning, if the ransom were not paid within a week, the hackers said they would delete the files that were held ransom.
According to Symantec, the WannaCry virus targets more than 175 file types, including website and server files, documents, photos, videos, music files, and many other common and less common file types.
The virus spreads within a network by scanning for other vulnerable computers once it gains access to a first computer. It also scans hosts on the Internet to spread as quickly as possible.
Microsoft introduced a patch for the vulnerabilities WannaCry exploits, but this can only be installed in advance of the virus.
WannaCry primarily targeted Russia, Ukraine and Taiwan, but also affected hospitals in the United Kingdom, universities in China, and worldwide businesses like FedEx and Nissan.
The WannaCry virus is just the latest example in how a cyberattack can take over a computer network and stop business. If you’re concerned about your company’s vulnerability, the team at Archetype SC can help. Our team provides managed services and security solutions for some of the largest companies in the world and have the knowledge and experience to assist your company.
The first step to securing your network and computers is a security assessment. Call Archetype SC at (843) 353-2929 to review your concerns or schedule your assessment today.
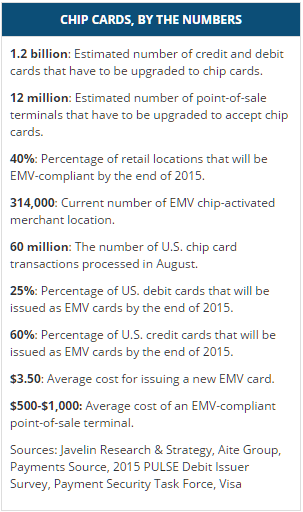
You likely have heard about the new shift in the credit card industry from magnetic strip to EMV chip cards. These cards have a small chip in them that facilitates communication to the payment card company in place of the magnetic strip technology that has been the industry standard for 25+ years. Historically, the motivating factor in large data breaches has been static data associated with payment cards. Once a thief breaks whatever security measure are in place and clones the magnetic strip of unsuspecting card holders that clone can be used over and over again which turn the fruits of the hacker’s labor into cash.
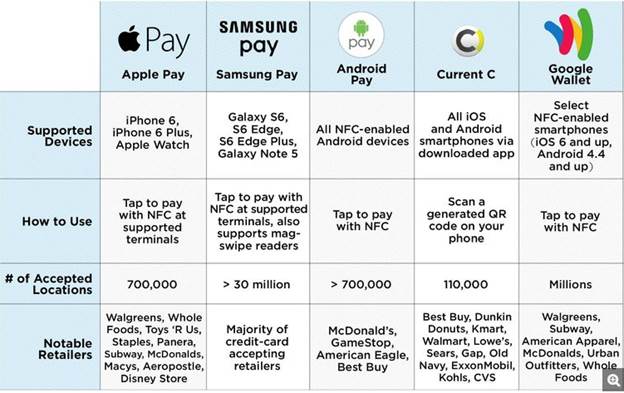
That is about to change once the swipe is replaced with the dip. The major security benefit of EMV is that every time you make a purchase, a new unique transaction ID is used to facilitate the transaction with the retailer. That transaction ID is unique to that sale and will never be used again, making the data retained by the retailer useless to a hacker. This payment model is the same deployed by mobile payment services like Android Pay, Apple Pay, and Samsung Pay. The difference between these three lies in how the information is transferred to the Point of Sale machine but the payment model of unique payment ID numbers is shared among them.
There will continue to be security risks, and EMV is not a cure-all pill. It does nothing to improve the security of online payments and not all retailers will have EMV POS machines at launch, leaving those retailers not only vulnerable, but heavy targets for hackers. Expect breaches aimed at smaller retail operations that do not have the means to upgrade their equipment at launch because EMV enabled cards can still be swiped if a POS machine is not able to process EMV payments. Europe has been using EMV for several years and credit card fraud has dropped by as much 80%, so it is clearly a step in the right direction.
Google’s Android, the most widely used operating system in the world, is going to be getting some more firepower. Into 2017 Google plans to roll key elements and features of its Chrome OS into the system, creating one platform for app developers and hardware makers to focus on building products.
Google’s aim is clearly to get Android running on as many devices as possible, it is already powering phones, tablets, watches, TVs, and car infotainment systems. Chromebooks, their relatively cheaper personal computers powered by the Chrome OS, account for less than 3% of personal computers. So making this shift isn't a seismic change that affects too many current users of the hardware, and it provides a new vertical for Android to grow into.
App development for Chrome OS was always lacking, as Google’s team didn’t dedicate resources in recent years to keep pushing the project forward. Only recently did they open Chrome OS up to supporting ported Android apps. 3rd party app developers didn’t have a lot of incentive to develop for Chrome OS with such a small market-share, and instead dedicated their time to Android.
Bringing the Google Play store to PCs opens an entirely new market for developers. A signal eco-system will allow developers to write an app once and know it can deployed across all devices without incurring significant development overhead and rewriting.
The move also could help Google and independent developers further break into the business world. One of the biggest successes of Apple’s iOS is the litany of workplace, financial, and productivity apps available for the iPad and Mac OS-powered Macbook. Many of these same type of apps exist for Android, and with cross-compatibility from a tablet to a laptop to a phone on the go, this could incentivize small businesses to make a more cost-friendly choice in hardware.
As with everything, Google especially, time will tell. But for now, rejoice that the confusing moniker of having a browser and an operating system both named "Chrome," long confusing public school teachers whose classrooms received Chromebooks as part of grants, is going the way of the dodo. The expected launch date for the first of these new Android powered PCs will be sometime in 2017, though preview builds are rumored to be coming as early as Q1 in 2016.
The InfoSec community has seen a rise in attention grabbing names for security vulnerabilities over the last couple years like Heartbleed, Freak, Shellshock, and now the latest android vulnerability Stagefright. The Stagefright exploit is different though, its name is derived from the media engine baked into android OS since version 2.2. The Stagefright engine is built into the application framework of android making it a part of your android OS no matter what country you live in, wireless carrier you use, or what brand of phone you buy. It is estimated there are 950 million devices vulnerable to a Stagefright attack.
The most alarming issue about this exploit is that it can be executed with no end-user interaction. An attacker simply has to send an mms message with malicious code written into a video and the device automatically begins to process the code, setting the attack in motion. Further complicating matters is most manufacturers default settings which are set to auto-retrieve mms messages. The user may not even know they were attacked because after the exploit gains root access of the phone the message is deleted but the malicious code stays.
The Stagefright media engine runs with system privileges on roughly 50 percent of the affected devices making it easy to gain root access to the device. Gaining root access on an android phone is the holy grail of exploits and the damage that can be caused is only limited by the attacker’s imagination.
Android is an open source OS which some might say makes it more secure while others would argue the opposite. The security architecture built into system applications in android take the sandbox approach. Most system apps are designed to be contained within themselves so attacks like the Stagefright exploit are not possible. This brings up the question of why the Stagefright engine has access to the internet and can be executed without the user’s knowledge. The answer is the DRM (Digital Rights Management) copyright control technologies that have been implemented over the last decade have required media players to make sure the content is being played legally. The technologies used to protect the content often require media players to check in via the internet, leaving a door open for malware.
Google has already began patching its Nexus line of phones and tablets with Samsung following as well. The inherent problem with android OS is that it is segmented into thousands of different variations of devices and carriers which makes patching a security hole like this a difficult task. Carriers like AT&T and Verizon control the software updates that get pushed out to their customers further complicating the matter. If there is a silver lining in this exploit being brought forth it is that Google and Samsung are going to begin delivering monthly security updates to devices. This is a step in the right direction for mobile device security.
Here is how to protect yourself from falling victim the Stagefright exploit:
Android Kitkat – Open the messenger app and in the settings menu select “block unknown senders”
Android Lollipop – Open the messenger app and turn off Auto-Retrieve for multimedia messages.
Black Hat, the organization that has been providing the IT industry with the latest in security research, development and trends for the better part of the last two decades, has done it again. Black Hat USA 2015 has come to a close. In traditional Black Hat fashion, researchers have left the security world buzzing about newly discovered exploits and vulnerabilities. These vulnerabilities cover the gambit of technology and range from new malware to vehicle hacking.
Malvertising (malicious advertising) has been the leading delivery method for malware by cybercriminals this year. The use of malvertising has increased by 260%. Malvertising is difficult to distinguish from legitimate banner advertising and has become a major concern. Many enterprises still struggle with end user education regarding e-mail phishing schemes. With the rapid growth in malware delivery via malvertising links enterprise will struggle once again to educate users and mitigate threats targeting both enterprise and BYO devices.
Researchers had a good time with Android this year reporting on two major vulnerabilities affecting nearly all versions of the platform. Stagefright, a vulnerability many are familiar with by now was the most alarming, hence the name. Basically, Stagefright is a mechanism (libStageFright) embedded in the Android OS that helps the system process video sent via MMS or Google’s Hangouts platforms. libStageFright is responsible for pre-loading video sent via MMS to improve the user experience. However, cybercriminals could embed an attack in the video that would in turn, launch automatically. This revelation has led smartphone manufactures and Google to lean towards monthly security updates (thank you). If your device is vulnerable and unpatched you can turn off the MMS auto-retrieve function. Another flaw in Android, though more complex to exploit, lives within the mobile Remote Support Tool (mSRT) apps. Basically, if a device is infected with malware that has mSRT permissions it leaves the device prone to be taken over by an attacker.
New cloud based man-in-the-middle attacks were presented. These attacks find cloud synchronization services (Google Drive, Box, Dropbox, etc) as their delivery method. While your cloud account credentials may remain secure, the tokens used to establish those sessions can easily be hijacked. Once attackers have the tokens it is an easy task to compromise files while they are being synced. In addition, cloud sync can be used to exfiltrate data and even send command and control communications.
Researchers also demonstrated how networked printers can be used to send data via radio signal a far enough distance to be compromised by an attacker. It is done by quickly power cycling the I/O pins on chips inside the printer. A signal can be generated that is strong enough to be picked up by receivers outside the building.
Additional research provided insight into vulnerabilities in internet connected vehicles using internet-aware Programmable Logic Controllers. SquareTrade card readers are vulnerable to an encryption bypassing hardware based attack. Vulnerabilities were discovered in Linux powered firearms allowing unauthorized control and discharge.
If you missed Black Hat USA 2015, more details about the above vulnerabilities (and others) can be found throughout various websites and in 6-9 months all research documentation will be released and can be found in the Black Hat Archives at https://www.blackhat.com/html/archives.html.
In light of all new vulnerabilities and research presented it is as important as ever to remain diligent and ensure that your security team is knowledgeable and well trained in identifying anomalies in your enterprise environment. If you would like an assessment of security conditions at your company, need help implementing solutions to risks, or are trying to recover from an attack, the team at Archetype SC is ready to help. Regardless of your size, our team of experts will help you establish a safer and more secure digital presence.
It should come as no surprise that Windows Server 2003 is entering End of Life on July 14th of this year. What should be surprising is that by some estimates, there are still over 10 million servers running this operating system. After its EOL, companies running Windows Server 2003 will have no support, and will receive no patches and no upgrades.
Without a doubt, opportunistic hackers will be doubling down on their efforts to find vulnerabilities and create exploits for this now-12-year-old operating system. Once vulnerability is found, if you are still running this OS, you will be unable to protect your servers from this threat.
There are many reasons why a company might still be running Windows Server 2003, not least of which is that it has proven to be a stable, reliable operating system that continues to run well on older hardware. Other reasons may include legacy applications and budgetary constraints. Whatever the reasons may be, continuing to run Windows Server 2003 exposes your applications, data and network to a significant level of risk.
Archetype SC can offer several services to help with your migration, making it as easy and cost-effective as possible. If a migration isn’t possible, we can help you protect your legacy systems by securing them through security assessments, network segmentation and network monitoring systems. Please see our services page for more information on how we can help you deal with this serious threat to your business.